RFID, WiFi and Bluetooth
30 okt. 2013RFID
Radio Frequency IDentification was initially researched in the 1940s, but did not go into commercial use until 1980s. Now billions of devices are tagged using this technology. It is used for identification and sometimes also for authentication. The system consists of a tag and it can be passive, semi-passive or active. We then have a reader or transceiver (both receive and send) capable of reading these tags from a distance ranging from almost touching to 10's of meters. Lastly the system need a database of the tags to keep track of changes.
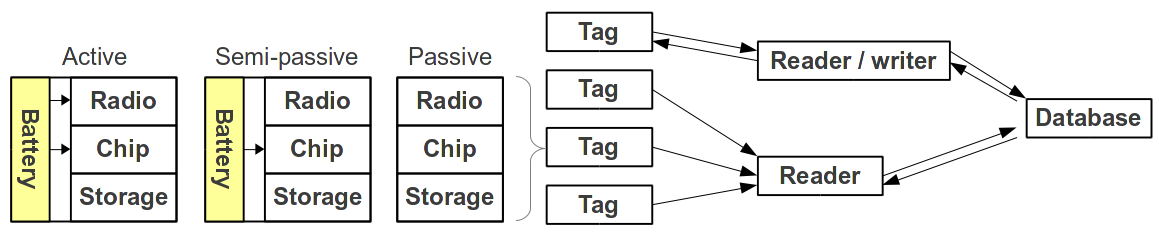
The different tags and other components in RFID
The setup time for a reader to access data from a tag is about 2 ms. Several standards exists depending on the usage area:
- Access control: Access to buildings and rooms based on authorization. Issued by companies and based on ISO 14443. It often uses larger ranges up to a couple of meters (vicinity) and most of these access cards use the MiFare technology using the broken Crypto-1 algorithm.
- Electronic passports: Is kind of the same thing, identification of people issued by states. Security is especially important for this one and for access control. The ICAO has standardized electronic passports ISO 14443. It uses the HF 13.56 MHz frequency, has about 10 cm reach (proximity), is modulated with ASK using either index of 100% or 10% (100% is "1" and 10% is "0"). The passport is passive. Passports use 3DES for transmission encryption, but the information is stored in the clear (you can simply read it also). The transmission key consists of the birth data + passport number + personal identity number. The key is read optically in a reader and then the transfer of digital data is performed using the keys now known.
- Ticketing: Payment of road toll, train and subway fairs are examples. Range must be fitted for the task and speed of reading is important, like for paying road toll in speed.
- "Point of sale" meaning reading of price tags, membership coupons etc.
- Inventory control: Tracking where individual units have been located, perhaps even temperature and shock in order to track down possible causes for bad products. Cost is of the tags is very important for this use case as everything down to the package of meat might be tagged. The ISO 18000-1 to 18000-7 is used for the radio part of this kind of logistics RFID, #6 most popular. Electronic Product Code EPC is a standard for how the data structures are defined and there are 6 classes of them. The difference between the classes are basically how re-writable they are and passive vs active.
In general for RFID we have the following security issues:
- Signal jamming: It is easy to jam the low powered signals, and this could be a potential problem, like in a store and train station, places with low physical security. It's all about signal to noise ratio and it should in theory be possible to achieve high signal to noise ratios being very close...
- Physical manipulation (spoofing) of tags: The information on tags themselves are typically not tamper resistant and can be read by force. Possible even written to. The main danger with this depends on use area. A tag with information for a smart phone could automatically lead to a malicious page and changing price and ID's in commercial situations and in inventory systems could cause problems.
- Spoofing (identity theft) of the ID, pretending to be a false ID is possible when no authentication is being used. Even with good authentication we get an additional problem with protecting and distributing keys. One could imagine copying the road toll ID of somebody and driving "free" at their cost. A system to discover this misuse could be built by knowing the location and time of usage and the licence plates could be captures for prosecution when anomalies are discovered.
- Eavesdropping: Can somebody read all close by passports, and even worse use this information to perform identify theft? Even when information is encrypted we still can use the meta data, the information of who is communicating for traffic analysis, and there are obvious privacy issues like learning the connection between electronic ID's and the person using them. A system with "randomly "changing ID's could be a solution.
WiFi
WiFi are the home and business networks dedicated for transparent cable-less access to home and corporate local area networks. The history is a bit messy, particularly when it comes to security. Lets first look at the access technology, then look at security.
Wi-Fi is standardized in IEEE 802.11 meaning a U.S. standard and this is a summary of the technologies used in the different variations:
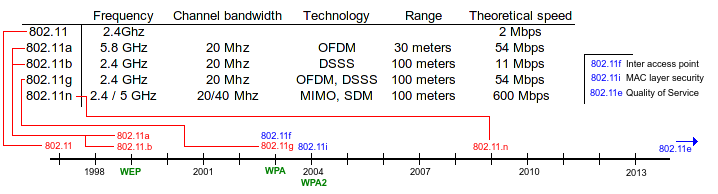
802.11 technology standards
Note that even though the range is said to be the same for all of the devices, the practical range is much less with obstacles in the way like floors and walls. 802.11n using MIMO has a lot of techniques for utilizing reflections and thus get much better signal qualities under difficult conditions compared to the older versions.
Two modes of operation is supported: Infrastructure and ad hoc. Ad hoc is simply peer-2-peer networks between standalone hosts and infrastructure requires dedicated access points. The standard 802.11f handles roaming between access points and the security is handled by different protocols. 802.11i specifies usage of AES, 802.1x (authentication) and SHA but was not available until 2004 and is what we now call WPA2.
With the introduction of 802.11a and 802.11b we got WEP, Wireless Equivalent Privacy and was intended to give us eavesdropping protection (encryption), access control (authentication) to the network and tampering protection (integrity verification).

How WEPs encryption and integrity works
Encryption is performed using RC4 initialized with a 24 bit initialization vector (IV) and either 40 or 104 bit keys (the most used, although more key sizes could be used). This results in 64 or 128-bit keys. RC4 is a good random number generator, but it takes some time to get going, meaning the first IV's are "weak". This is partly the reason why we can break WEP in minutes nowadays. Being 24 bit also means that we must reuse them often with a fast connection. Every 5000 packets was claimed in the lecture, and this means that the probability is more than 50% of picking 2 equal when picking 5000 out of the full set of 2^24. See Birthday problem, and note we are talking about finding two persons with the same birthday, not another person with the same birthday as us). The key is pre-shared and it is shared for all users on the network (at least for home networks). See Wikipedia for the RC4 PRNG. Using the IV in counter mode is better than random as we are guaranteed no collisions until it wraps around.
Using CRC-32 is very bad as it's linearly dependent on the input. The authentication is totally broken and should be turned off.
WPA came out before 802.11i were ready and was a patch for WEP. It added TKIP (Temporal Key Integrity Protocol) so that the master key were not used directly with RC4 and also ensured rapid key schedules, and replaced the. The IV was doubled to 48-bit. HMAC is used for message authentication checks using MD5 or SHA-1 instead of CRC-32. WPA can be used in enterprise mode using a RADIUS server that assigns transmission keys based on username and password. In the consumer version the key must be manually distributed, but the entry key is only used the first time, and at first access the client is allocated a new random key unique for that machine. This avoids intercepting other users data.
WPA2 is the full implementation of 802.11i (it was actually implemented before the standard was settled) and adds the AES cipher in counter mode and even stronger message authentication codes (AES in CBC-MAC mode). WPS (Wifi Protected Setup) is a convenient way to get devices on the network that has known flaws and should be disabled.
Bluetooth
The motivation for Bluetooth was to remove the need for cables. Typical use areas are wireless mouse, keyboard, handsets and communication between phones and phone-computer. The standard is 802.15.1 and implements a pico-net with 8 users where one is the master and the others are slaves. It uses FHSS (Frequency Hopping Spread Spectrum) at 2.4GHz with 1600 hops per second, and can transfer around 800 kbps connection-less that can be divided between upload and download. It also has a connection-oriented mode for voice that is 64kbps using PCA or delta modulation.
According to lecture material, there are 3 modes of security and is implemented in the stack using a link manager (link setup, authentication) and security manager together with some databases or paired devices. The first mode does not do much security at all, but the device will respond to authentication requests. The 2nd mode "Service Level Security" is when security is is established after the connection is initiated (above link layer), while mode 3 is encryption before channel establishment (on link layer). A 4th mode exists in version 2.1 and above. Selected mode is dependent on the manufacturing choice and the purpose of the item. One can argue that the keyboard requires more security than a mouse device.
A device must be paired with the master (like a mobile phone) before it is allowed access. Every Bluetooth device has a unique device address of 48 bit and a pin between 8 and 128 bit. These pins can be set on more advances devices and are fixed for simpler ones. This illustration explains the process using the SAFER+ bag of algorithms E0, E1, E21, E22 and E3:
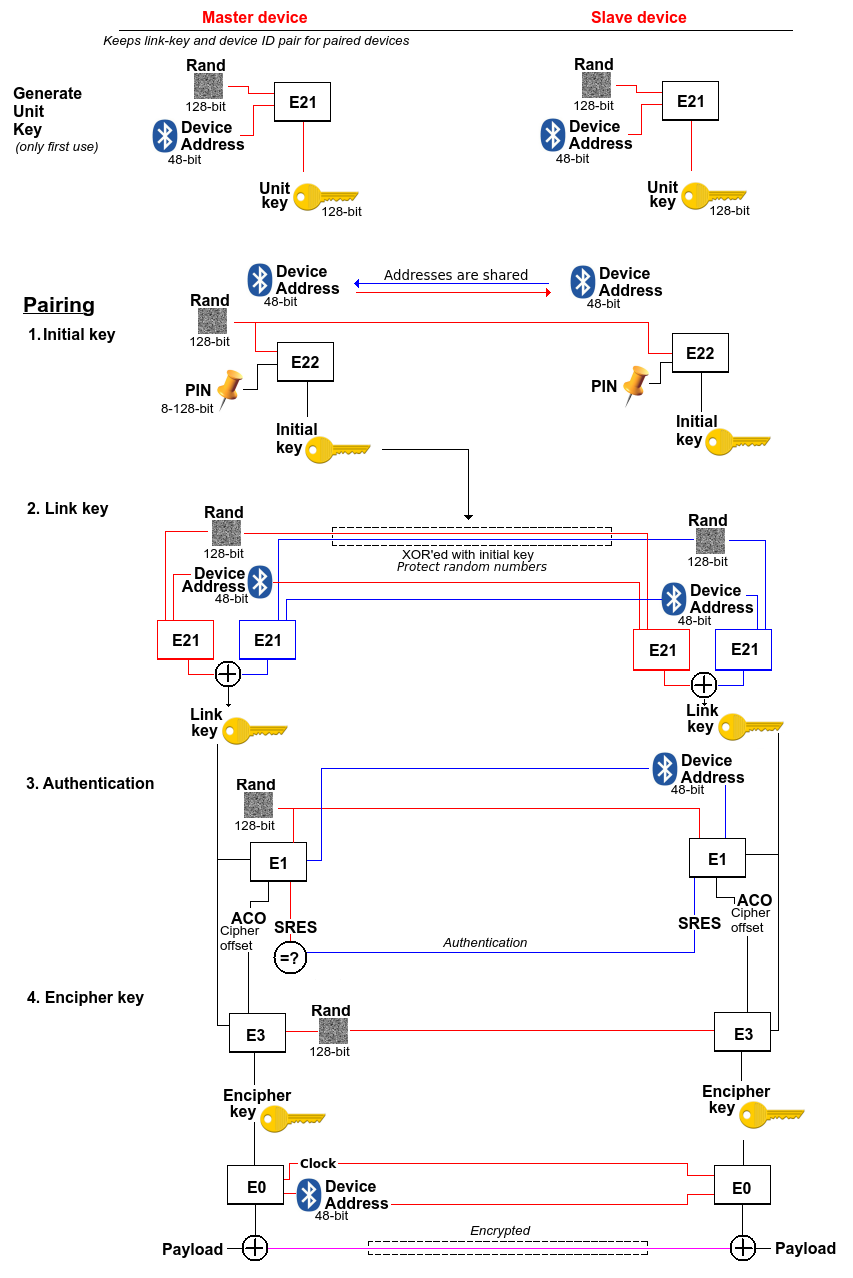
Illustration of Bluetooth pairing, based on lecture material
As we can see from the procedure in the figure, note that the unit key is not being used at all. For weaker devices (less powerful) it can be used instead of the link-key for authentication (and thus generation of encryption key). The unit key is claimed to be public, which means using the unit key instead of the init-key opens up for spoofing attacks.
Security issues include:
- Short PIN's
- Some weaknesses in SAFER+ (The E0 encryption algorithm)
- Strength of pseudo random number generator not known
- Bluejacking, bluebugging and car whisperer (see howstuffworks.com)
