DF2: Reverse engineering part 2
28 mai 2013This lecture continues from the last one (anonymity, antivirus) and continues with describing lab setups used for analyzing malware manually and automatically. I would recommend having a look at Cuckoo sandbox and Malwr.com for concrete examples.
Repetition case: Lab setups for analyzing malware (malware using anonymization techniques) and how to identify domains and IP addresses used by malware. See part 1 on reverse engineering.
Malware Analyst's Cookbook and DVD: Tools and Techniques for Fighting Malicious Code
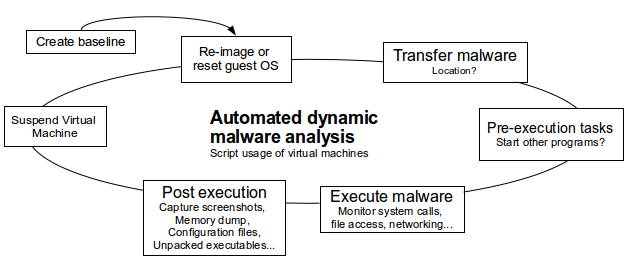
- Ch8: Automate malware analysis (using VM's): Interesting papers on page 241 (Automating malware analysis, Mass malware analysis: Do it youself kit, HIVE: honeynet infrastructure), SandboxIE application sandbox

- Ch9: Dynamic analysis: Monitor executing malware in an controlled environment. Hook based, difference based and notification based.
Hook: API hooking (staling API call in malware, page 303), Avoiding process termination, file deletion (preservation) and driver loading, logging shell activity. MS detour API (See my Software Security Trends project).
Difference: Registry changes (added, removed, updated)
Notification: Process monitor - ToD, Process, PID, Operation, Path, Result, Details - Ch10: Malware forensics: What to look for when trying to spot infections. C library Sleuth kit (TSK: alternate data streams, MMLS: partitions, FLS: show files, ISTAT: extended information, ICAT: get file..), automate/script sleuth kit, backdating files, script for cross validation of files (tsk-xview.exe page 347), Sysinternal RootkitRevealer, Sysinternal handle.exe, (Process hacker to unload DLL), GMER root kit scanner, HTML injection, Regripper pyhton plugin.
- Ch11: Debugging malware: Change/manipulate run-time behavior (compared to only looking at what is does) immunity (python API), OllyDbg, Windbg, IDA pro, breakpoints and change of flow. Different from debugging when programming (because you have the source). Tedious and required a lot of experience.
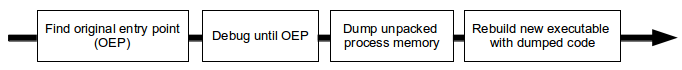
- Ch12: De-obfuscation: Encoding, Encryption (find the key - memory dump?) and packing are known means. Revert XOR and base64 encodings. Unpacking malware:

- Ch13: Working with DLL's: A DLL is code without the framework around in order to but it in memory and run it. One can use rundll32.exe or similar for 64-bit (on Windows) to run any function exported by the DLL. DLL's run inside of processes, and gives malware the possibility to "hide" inside other (host) processes. Programs like CFF Explorer, Pefile, API monitor, Process monitor, Task explorer.. or try a debugger.
- Ch14: Kernel debugging: Subversion on tree levels: program, library and kernel. For debugging malware attacking the kernel we can use a trusted system and debug remotely. Local kernel debugging is possible but not recommended. Tools like Windows Driver Kit (WDK), Symbols (from Microsoft) or LiveKD. Understanding crash dumps might be related. Inspect the memory structures (processes, threads, loaded modules, import tables, handles etc) directly in ram and compare it to what the kernel claims.
- Ch15: Memory forensics (Volatility): Be careful where to store the memory dump, network (netcat) disk good idea. Remember to encrypt (ssh). Contains runtime information lost when turning of the system. Memory is always changing, and freezing it is not easy. A buss attack (firewire) is a good way to access the memory (because of DMA access). Tools: MoonSols Windows Memory Toolkit (old win32dd) and can also convert between crash dumps and hibernation files. Volatility can enumerate processes, visualize with graphviz, rebuild PE files (Windows executable). F-Response is a server-client model where one can read-only mount memory and disks of remote systems.
- Ch16: Memory code injection and Ch17: Memory rootkits: Rootkits will hide files, processes, registry entries, ports, connections etc. API hooking is one way to do it. Rootkits can also manipulate the memory directly (the structures in memory used by the kernel)
- Ch18: Memory network and registry: Detect promiscuous mode (sniffing mode - accept all packages), Difference between registry in memory and on disk.
Snarveier
Flere fra skole