Seminar no1
9 jan. 2014The agenda for this meeting was:
- Introduction
- A motivation lecture
- How to write the master thesis
- Citing and plagiarism
- Practical information
Kowalski introduced with a social-technical view on security with focus on the different ways to defend (based on a slide from one of his publications):
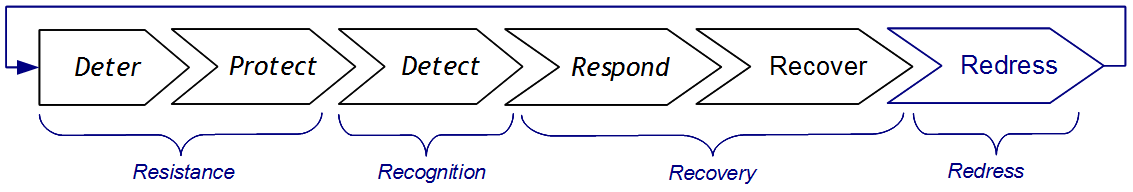
Added some blue stuff to it based on lectures from forensic readiness
and he talk about the difference between what can be automated and what should be automated. We should focus on what can.
This figure/model is actually quite interesting, and the concept is that resources must be divided between the blocks. One could imagine a rule such as "tree climbing is forbidden!".
- One way to deal with the problem is via protection. Have armed police officers guard each tree and shoot people trying to climb on sight. One might guess this would be quite expensive.
- Another way to deal with the problem is with deterrence: make the rule a law punishable by 2 years in prison. This might be enough to stop most people, and by having some level of detection and redress capability the rule could be handled. The significant trade off is the level of detection.
- Still another take on this is the realization that the reason for the rule might be the damage to the trees because of broken branches. Instead of trying to stop people from climbing, perhaps all the resources should go into tree recovery..?
For information security, the goal is to exploit information and limit opponents from doing the same. Redress is typically hard because of the global nature of our infrastructure and because of a variety of laws and regulations. Protection and recovery has thus been one of the core focus areas till now. We see a trend focusing more on detection and including the business operational context when dealing with security decisions.
The motivation and plagiarism lectures were quite dull and served mostly as repetition except for the tip of looking for published journals instead of citing books in general. It is assumed what is cited has been read.
The "how to write the master thesis" lecture had some interesting additions:
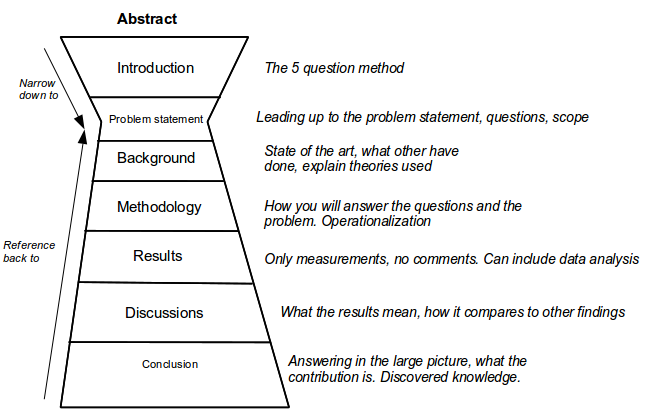
We went through the "5 why's" with a student example and the goal was to illustrate the need to always question why for every answer to both understand the big picture and to narrow down. Always cite other sources in addition to claiming something is a problem.
Lastly we were reminded of a lot of administrative documents to read in Fronter, check our hig.no e-mail regularly, deliver extended abstract and write contract with supervisor(s). Remember the contract with the library for publishing is in addition to the contract with the supervisor.