3G cellular
6 nov. 2013UMTS technology
The 2G GSM technology was very popular reaching about 3 billion people, but had problems scaling around year 2000. The 3GPP standardized 3G for most of the world around (Europe, Japan, South Korea, China) year 1998-2000 with UMTS, while the Americans (3GPP2) did a similar thing for USA. The main difference is that Europe/GSM went from a TDMA based radio system to WCDMA (Wideband CDMA), while USA already had CDMA in IS-95 (CDMAOne) and simply evolved to CDMA2000. They also has access to satellites making synchronization of time (GPS) easy.
Availability of 3G started around 2003. There is a new release by 3GPP every year. Another interesting fact is that GSM used a stream cipher, UMTS (3G-standard) uses a block cipher (KASUMI) while the 4G uses a stream cipher again (SNOW).
UMTS is the focus of this course. There are several improvements, including speed, packet switching support, and security aspects such as 2 way authentication and stronger encryption throughout the system.
UMTS = Universal Mobile Telecommunication System (Europe/Asia)
UMTS consists of 3 main components, similar to the GSM structure: The user equipment (UE), local radio access network (RAN) and the core network (CN).
The core (CN) network now contains 2 domains, one for voice / circuit switching and one for data / packet switching. The core network is also divided in a serving network and a home network so that these functions can be divided between mobile network operators when roaming. Note that the packet switching SGSN has a similar role as MSC and VLR in GSM.
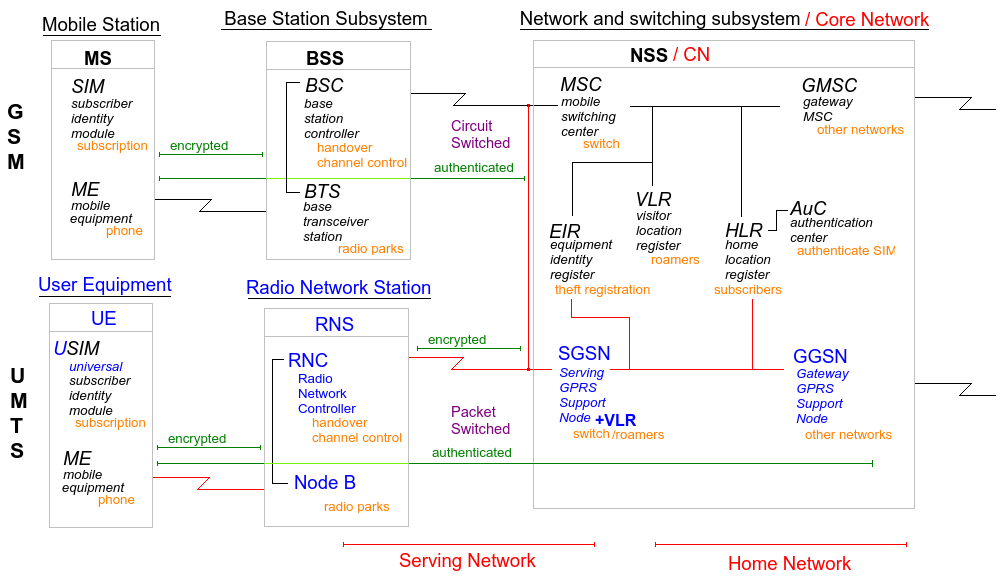
The new names for components in UMTS. Note the dual role of SGSN.
The user equipments (UE) subscriber identification module (SIM) were upgraded / evolved to USIM (universal SIM), but keeps similar data such as secrets and management data. In UMTS more features are baked in allowing the user equipment to talk to both the access network (RAN) using the access stratum and the core network (CN) using the non-access stratum. Stratum is a fancy word for layer.
The access network (RAN) has now two types: UMTS Terrestrial Radio Access Network (UTRAN) and GSM/EDGE Radio Access Network (GERAN). In UTRAN a user equipment can be connected to more than one base station at the same time (micro-diversity), useful for roaming.
Data rates in UMTS was originally 144 - 2048 kbps depending on being in a rural, suburban or urban area. The rates were upgraded to 14,400 kbps with HSPA (HSDPA, HSUPA) and 42,000 kbps with HSPA+ (HSPA evolved).
Protocols in UMTS are:
- Communication Manager (CM): Call handling and session management. In none-access stratum.
- Mobility Management (MM): Mobility and security, like paging (finding a user). In the access stratum. This function is handled independently in the packet switched and circuit switched domains and might affect the security.
- Radio Resource Management (RRM): Power control, handover and system load. Divided between access and non-access stratum. Handover can be hard meaning the connection is terminated and a new one is established. It can also be soft using the macro-diversity property of being connected to several cells at the same time. Power control is all about making sure all users send with a power level so that is it received with the same level at the base station. This to avoid inter signal jamming (near-far problem. It is most important for uplink. It is also performed for downlink to protect against interference between other cells. Power is checked 1500 times per second and we have slow open loop (link setup performed by user equipment based on pilot signal) and fast closed loop (measure at base station and power commands) checks.
- IP is used on the packet switched domain and UDP is preferred. The GPRS tunneling protocol (GTP) uses IP/UDP to carry requests to the Internet. Complexities of the power management makes it very easy to jam UMTS.
- Packet Data Protocol (PDP) is used for session management, addresses quality of service.
WCDMA has two variations: Frequency Division Duplex (FDD) and Time Division Duplex (TDD). FDD use 1920-1980 MHz for uplink and 2110-2170 MHz for downlink. TDD uses 1900-1920 MHz and 1980-1995 MHz but don't separate between up and down link.
One channel is 5 MHz, but only 3.84 are effectively used because of guard bands. The American version CDMA2000 uses 1.25 MHz channels. CDMA2000 also uses GPS to synchronize time between cells, and since UMTS does not, additional technicalities such as cell search and handover must be handled. User/cell separation "scramble" codes, channel/user "channelization" codes and the resulting combined "spreading codes" is used to key the CDMA.
The WCDMA frame is 10 ms, and consists of 15 time slots. Convolution and turbo codes are used to correct transmission errors, and uses the "Rake" receiver making use of multi path propagation.
UMTS security
2G GSM weaknesses
- Authentication: It's possible to fake a BTS (base station) because it is not authenticated. Authentication data is not protected between the base station and the core network. Authentication data is small in bit size.
- The user data is unprotected between the base station and inwards in the network. It can even be turned off in the air from the BTS to the mobile equipment. The encryption algorithms are weak. Short encryption keys are also a problem.
- There is no data integrity checks.
The security goals in 3G (UMTS) security was to adequately protect user generated data, resources and services and make world wide roaming easy by having the same security standard in the back end.
Design principles were to build on existing 2G technology and add:
- Increased authentication security, two way.
- Always encipher the radio interface and also protect data in transit in the core network
- Continue protecting the identity of the user, including the IMEI (phone hardware ID)
- Limited trust in visitor networks
- Upgrade the SIM to USIM
- Increase key lengths for stronger authentication and encipherment
- Add integrity "mechanisms" for the IMEI number (?)
3G security were divided in
- network access: Mostly encipherment and authentication.
- network domain: Securing data between home location and the current serving location.
- user domain: Protection of access to the mobile equipment.
- application: Protection of content (SMS, MMS etc?) between applications and the service provider.
- visibility and configuration: Show the user that security is enabled.
3G UMTS identities
These numbers enable identification:
- IMSI: International Mobile Subscriber Identity. Protected using TMSI: Temporary IMSI and P-TMSI: Same but for packet-switched part
- TLLI: Temporary Logical Link Identity
- MSISDN: Mobile Subscriber ISDN
- IMEI: International Mobile station Equipment Identity
- IMEISV: IMEI Software Version
3G UMTS authentication
In order to establish 2 way authentication and less trust in the serving network, potentially due to roaming, we have the IMSI forwarded to the AuC in the home environment (where your subscription belongs). They will check if the serving network is allowed and if it is give it a RANDom number, an AUTN authentication token, the XRES (eXpected response), the encipherment key CK and integrity key IK. The random number and the authentication token is sent to the USIM card in the mobile equipment where the AUTN is verified and if then RES is sent back used by the serving network to check if the user is allowed service. The USIM generated CK and IK and gives it to the mobile equipment while the CK and IK received from the home AuC is sent to the Radio Network Station where encipherment and integrity checks is started. The mobile equipment also gets a temporary IMSI so that it's identity is hidden from now on.
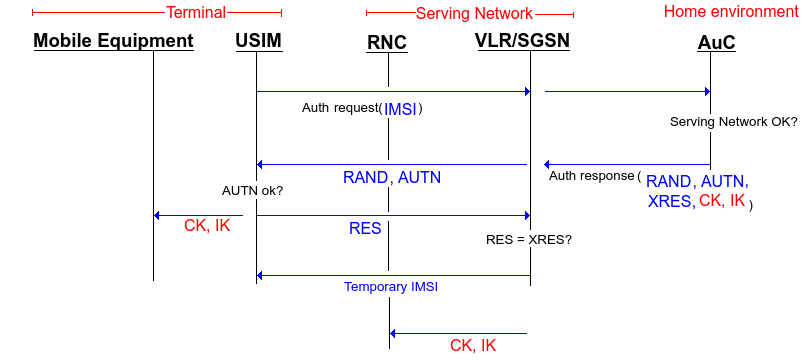
General overview of 2-way authentication in UMTS
In the previous figure, no explanation were given for the authentication response by the home AuC. This is how these 5 parameters are calculated:
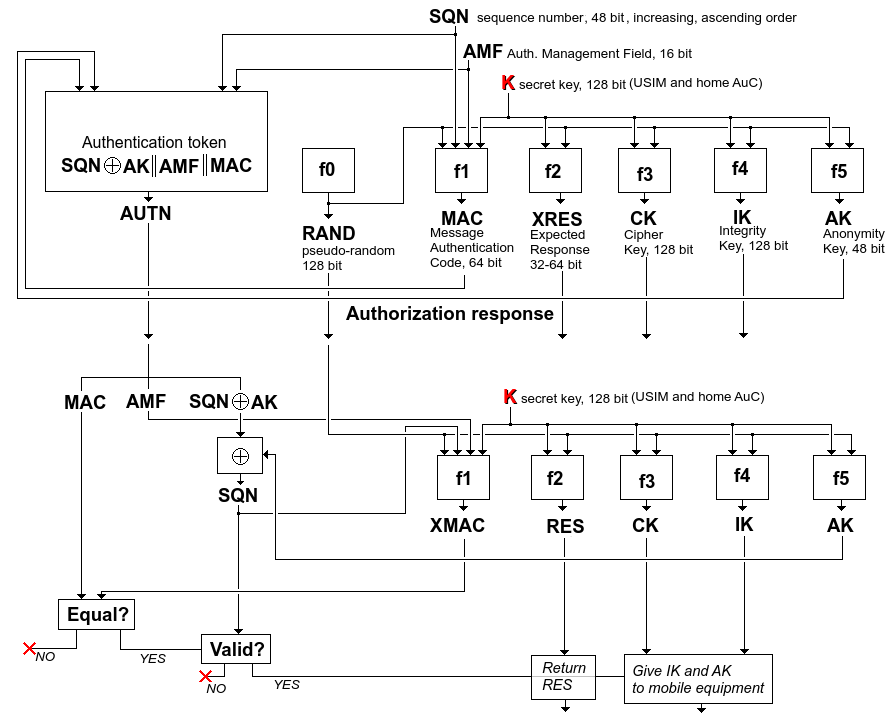
Note the XOR of the SQN and AK. This is to protect the SQN and since the USIM will be able to calculate AK, it can find SQN and verify it.
When this is run on the USIM, f5 must be run before f1 as SQN is "hidden" by AK. f1 will then output XMAC (expected MAC) and compared with the MAC from the authentication response. If they are equal then SQN is verified and RES (output of f2) is sent back for comparison with XRES.
The SQN can get out of synchronization between the USIM and the AuC. If this happen, then a protocol involving a parameter AUTS with SQN from the USIM enciphered with the master key together with a MAC value using in addition a random number and a default AMF*. Special f1* and f5* functions are used:
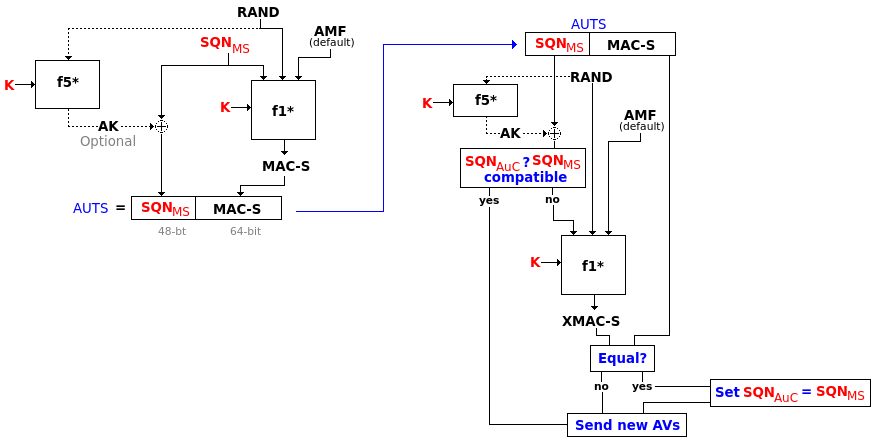
Synchronization steps using AUTS requests
MILENAGE is the default algorithm functions for all the f-functions and is based on a chained AES block cipher. It uses the key, something called operator variant (same size), and is initiated with SQN and AMF. Output at different stages result in the f1 to f5 including f1* and f5* as illustrated bellow:
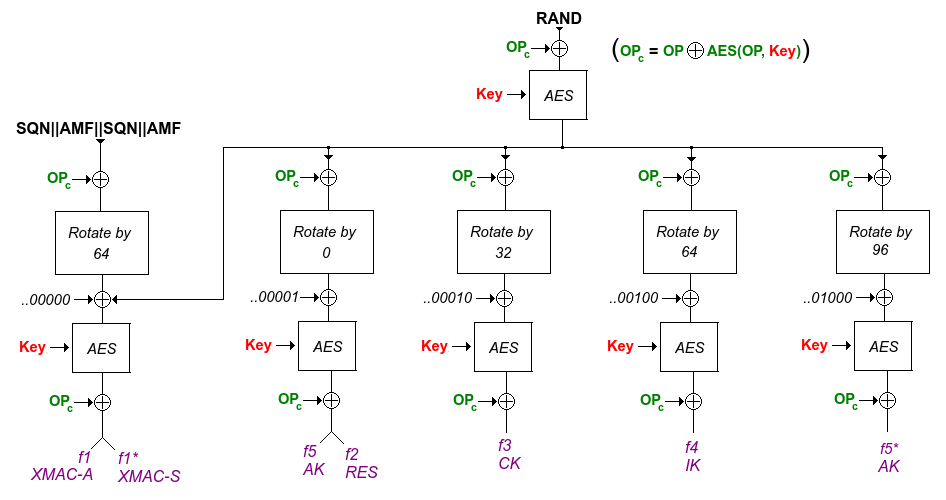
How the f1 to f5 are constructed
3G UMTS encipherment
f8 is used for encipherment. It can operate in RLC (radio link control), UM (unacknowledged mode) and AM (acknowledged mode). It is keyed by COUNT-C, BEARER, DIRECTION and LENGTH in addition to the CK (generated in the authentication step). Output is XOR'ed with the plain text as usual.
C-COUNT is time dependent, 32 bit.
BEARER is for using the same key with different radio bearers of the single user, 5 bit.
DIRECTION is 1 bit, up- and downlink, avoid using the same key for the different directions.
LENGTH is 16 bit and the length of the key stream generated.
In 3GPP f8 is the block cipher KASUMI in a combined OFB (output feedback mode) and CM (counter mode).
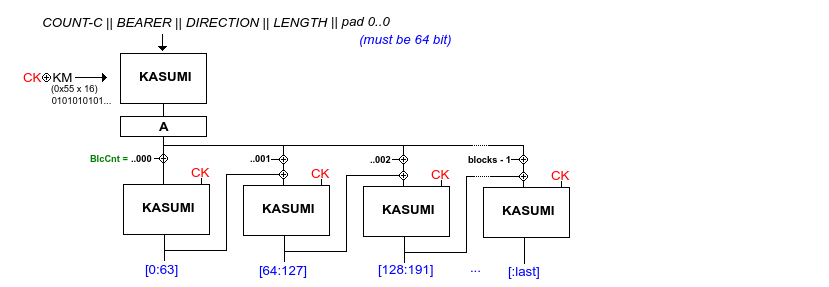
Same illustration as for 2G GMS A5/3 and GPRS
3G UMTS integrity
f9 is the integrity algorithm. It generates a message authentication code called MAC-I (so not to confuse it with the one in the authentication process) of 32 bit. It uses COUNT-I, FRESH, MESSAGE and DIRECTION as input in addition to the IK (integrity key) from the authentication process.
COUNT-I is 32 bit and is frame dependent, protection against replay
FRESH is a 32 bit nonce
MESSAGE is the message, as long as one wishes
DIRECTION is still uplink or downlink
It is also based on the KASUMI block cipher in CBC (cipher block chaining) mode like this:
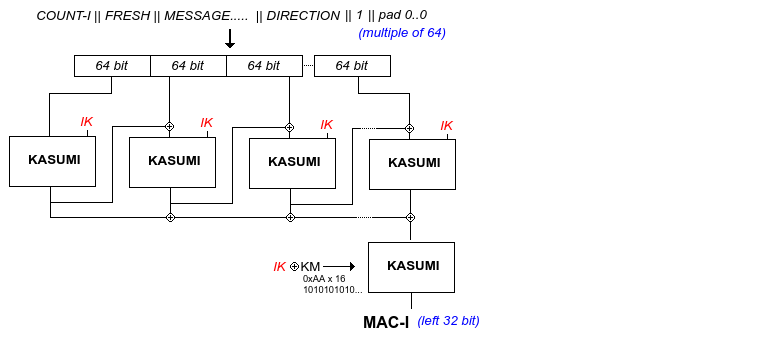
Generation of MAC
3G f8 and f9 algorithms
2001: Claim of proof of security of f9 (against linear differentiation analysis attacks)
2003: Proof for f9 were proved wrong and f8 concluded not possible to prove secure.
2005: Modifications f8+ and f9+ proved to be secure. Only change was to set KM to 0. KM is the value originally set to 0x55 or 0xAA times 16. One might wonder what happened here...