Wireless theory and security
23 okt. 2013Wireless theory
Wireless communication is based on electromagnetic waves. We know electricity (E) and magnetism (B) are tightly related and that these waves also have particle properties (photons). Every wave can be described by:
- Amplitude: power or height of the signal. The intensity of a signal is measured in [W/m².]
- Frequency or wavelength: describing the number of oscillation per second.
- Speed: determined by medium (magnetic permeability and electric permittivity), never observed greater than C = 299,792,458 [m/s]. About 2/3 of C in copper and fiber channels.
- Polarity: The orientation of the magnetic and electric field as they are orthogonal (90° separation).
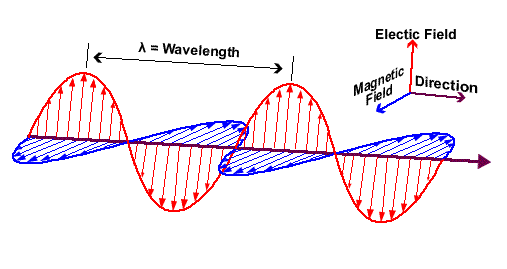
http://www.ndt-ed.org/EducationResources/CommunityCollege/RadiationSafety/theory/nature.htm
In addition, if given a reference wave, we can measure the phase as the lag to the reference. We know waves, described by the sinus function is back at the beginning after a wavelength (2π) so the number will be a degree between 0° and 360° [-180° and 180°]. The waveform must not be perfectly sinus.
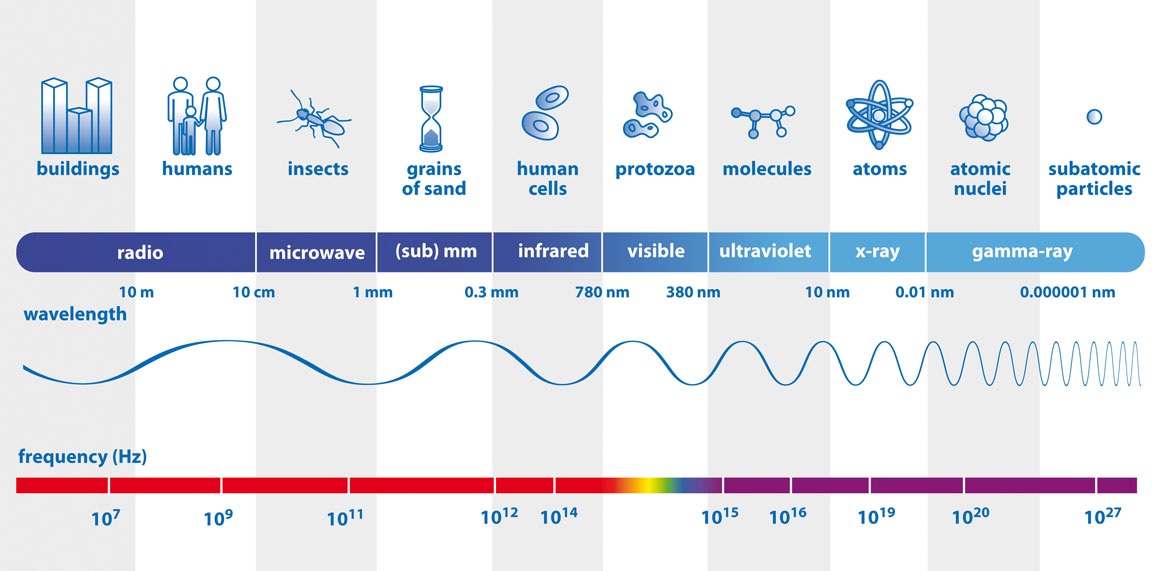
http://www.universetoday.com/101885/the-curious-channel-37-must-see-tv-for-radio-astronomy/
Twisted pair operated from the beginning of the spectrum, few Hertz up to about 300 MHz, almost UHF.
Coax goes a little further, up till about 1 GHz or halfway UHF.
Optical fibers operate around 300 THz or in the visible light region of the spectrum.
These spectra are human made up and there is absolutely no difference between the waves in the different spectra except for their frequency. That being said, high frequency waves react differently on other particles than do lower frequency. High frequency has much greater penetration ability and can cause damage, like the ultra violet rays from the sun and the microwaves used for heating food. Higher frequencies also tent not to reflect or bend as easily as lower frequencies and this is the reason why short wavelength radio like HF and lower can travel around the globe because of reflections in the ionosphere. These waves can also bend with the surface of the earth and follow the curvature to some extent.
Of historic interest we used to reserve the band 533 - 1,700 KHz for amplitude modulated (AM) radio, 88-108 MHz for frequency modulated (FM) radio (still in use) and 54-88 + 174-220 MHz for television broadcast. More and more of these legacy services are being digitized and places as services on top of common carriers like over Internet. Allocation of frequency bands is a hot topic as the need is high and the availability is scares.
Analogue signals in the base band, like a sound signal from 1 Hz up 20-25,000 Hz, was traditionally modulated on to a carrier frequency using amplitude or frequency modulation (AM/FM). Phase modulation is a possibility, but were not used that much because it requires a complex receiver. The digital analogy is keying, like Amplitude-shift keying (ASK), Frequency-shift-keying (FSK) and phase-shift-keying (PSK)
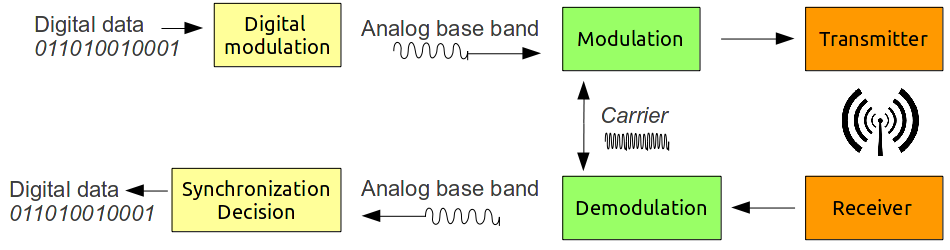
Based on slides
In ASK (OOK) we vary the amplitude depending on a binary signal (0 or 1). In FSK we vary between two frequencies depending on the binary signal. In PSK we send a "normal" signal and a shifted signal separated by half a wavelength. PSK can be coherent always referring to the original phase (perhaps sent in a preamble) and it can be differential meaning the previous interval sets the phase standard and same or different than last determines the bit sent.
We can use smaller phase delays like 90°, 45° and 22.5° and we can also have multiple amplitude levels in order to send more bits [bit-rate] per symbol [baud-rate]. QPSK is when using 4 phase levels in PSK. QAM is a confusing term as it suggest we have 4 levels of signal strength using amplitude modulation, but in fact it is a mix of amplitude and phase modulation allowing combinations. 16-QAM is mentioned as an example using 4 levels of amplitude (0%, 33%, 75% and 100%) and 4 phases 0°, 90°, 180°, 270° totaling 16 combinations and thus 4 bits per symbol. Constellations are graphical ways to represent this.
Spread spectrum is a technique used for distributing the information in a signal over more bandwidth. Two types: Direct sequence spread-spectrum (DSSS) where the original signal is mixed with pseudo random noise at a much higher rate than the information source and frequency hopping spread-spectrum (FHSS) where the modulation signal is changes rapidly determined by a pseudo random source. The rate of pseudo random noise is called chip rate. The benefits are jamming resistance (better signal to noise ratio) and we can hide signal in the noise (white noise all around us).
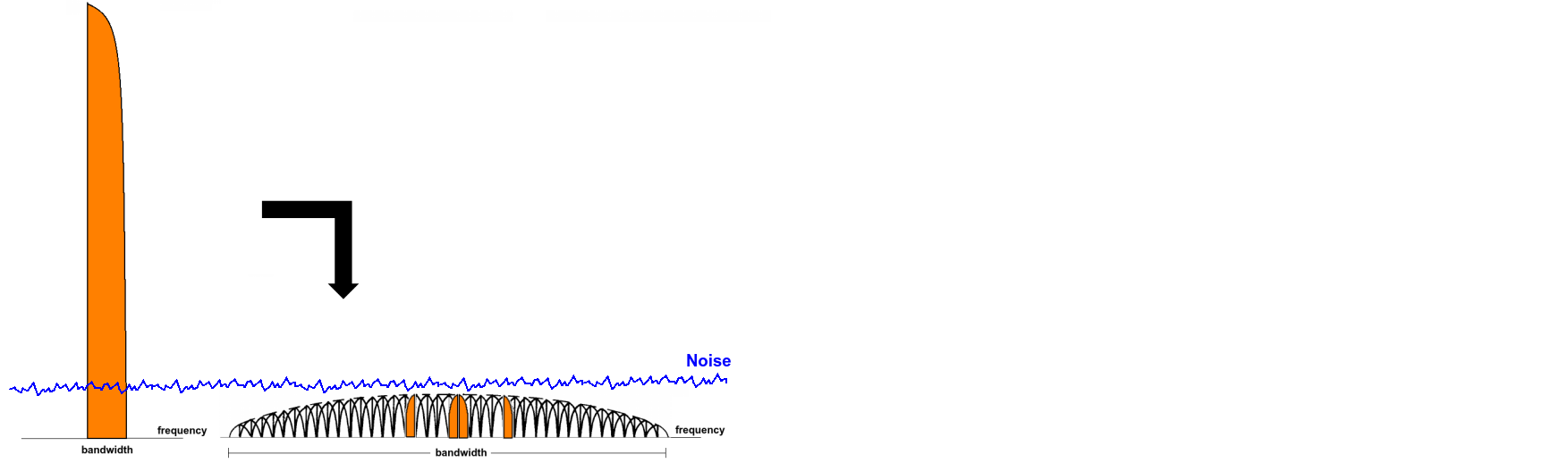
Based on slides
Next tree letter abbreviation is OFDM or orthogonal frequency division multiplex. It is used in the later WiFi 802.11g/n, in WiMAX and LTE (more on them later). The motivation was better frequency interference protection and multi-path (reflection) resistance. Multi-path problems happen at high baud rate, and in order to increase the bit-rate we can increase the baud-rate, the number of bites per symbol or we can have multiple carriers. This is the concept of OFDM. 802.11g uses 250 symbols of 6 bit (64-QAM) per sec, has 48 sub-carriers, and the coding rate (payload / all data sent) is 3 of 4. This gives 54Mb/s (mega bit per second). The sub-carriers are overlapping but it's OK since the frequencies are orthogonal meaning when one is max, the others are 0 (or close to).
OFDM is similar to CDMA or code division multiple access where frequencies are used in a pattern determines by a code with small chance of collision. OFDM assigns different sub-carriers to different users (the base station does?). MIMO or multiple input multiple output is basically a system with several antennas for sending and receiving.
Because numbers vary from very small to very large, it is normal to use decibel. dB = 10 * log( effect 1 | effect 2)
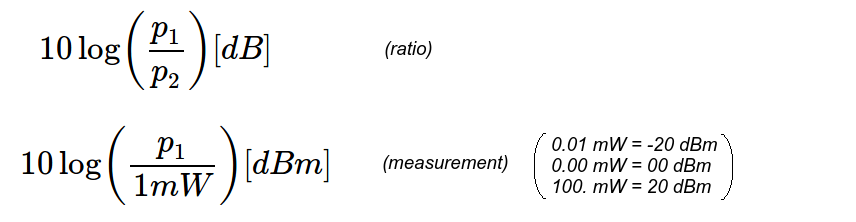
Based on slides
Basic security concepts
What is the relationship between a vulnerability, a threat and an attack / exploit? A vulnerability is a weakness in design or configuration. Can be intentional, by mistake or by chance. A threat is traditionally someone or something capable of finding and utilizing vulnerabilities, but here it was defined as an event that can disrupt functioning, integrity or availability of a network. Attack or exploit is still a specific instance of a vulnerability being utilized.
What must be protected:
- Confidentiality, integrity and availability (CIA-properties)
- Privacy: user identity, location, usage
- Authentication: Protect access to the network (kind of integrity of the network?)
- Access control: Just the mechanism to ensure protected access to the network
- Non-repudiation: Typically not an issue at the network layer, but still important for signing messages and avoiding possibility of saying "I did not do or send this".
Types of attack:
- Passive attacks
- Channel eavesdropping (listening in on content - mitigated by encryption, traffic analysis of meta data)
- Channel overuse (channel is shared and the sharing is not fair - mitigated by blocking or quotation)
- Channel eavesdropping (listening in on content - mitigated by encryption, traffic analysis of meta data)
- Active attacks
- Jamming (denial of service)
- Data alteration (modify content in-air) (man in the middle)
- Identity cheat (impersonation of legitimate user - false access, spoofing)
- Jamming (denial of service)
Specific vulnerabilities of wireless mobile devices are that the are small and has little processing capabilities and power, like an RFID chip. They can easily be stolen.
Wireless technologies
- RFID: Reading ID numbers and storing small amounts of data, powered by reader, used for logistics and ticketing.
- Personal networks like Bluetooth (802.15.1) and ZigBee (802.15.4): Short range cable replacement technology, low bit-rate. ZigBee even lower but can connect more devices.
- Wireless LAN (802.11): Transmit data between high speed devices.
- Cellular networks like GSM (2G), UMTS (3G), HSPA, LTE (EPS) and WiMAX (802.16) (almost 4G): Originally telephony, but moving more towards the role of the wireless LAN, except for a much wider coverage area (WAN). Some important abbreviations:
- SIM/USIM: (universal) subscriber identity module
- MS/ME: mobile station/equipment (phone or modem)
- TU/UE: terminal unit or user equipment (MS and SIM or ME and USIM)
- BTS/"Node B": base transceiver station or equivalent
- BSC/RNC: base station controller or radio network controller
- BSS/RNS: collection of BTS and BSC or "Node B" and RNS
- MSC: mobile switching center
- GMSC: gateway for MSC
- SGSN: serving GPRS support node
- GGSN: gateway GPRS support node
- VLR: visiting location register
- EIR: home location register
- HLR: equipment identity register
- AuC: authentication center
- PSTN: public switched telephone network (1G)
- PLMN: public land mobile network
- SIM/USIM: (universal) subscriber identity module
Speed ...towards 4G
3G has 384kbs bit-rate. HSPA(+) (high speed packet access) allows for users to share channels to increase this speed. Goal is to move from circuit-switched to packet-switched networks and use voice over IP. Long term evolution (LTE) as mentioned before is only based on packet switching. Evolved packet system (EPS) is basically the same (newer) thing. Increase up to 100 mbps is the goal for what to be called 4G. WiMAX is a cheaper alternative using other frequencies than UMTS/LTE.
Network types
Mesh: Many routers so that any one node can be lost (Internet today). Wireless mesh network usually have fixed access points.
Ad-hoc: Self-configuring (moving) access points routing autonomously. (MANET)
Hybrid ad-hoc: Nodes other than access points can also route information using multi-hop communication so that being in coverage of an access point it not necessary.
Vehicular networks: Communication between moving object and base station, but also autonomously like car to car communication for collision avoidance.
Wireless sensor networks: just a mobile sensor...
Integrated networks: Mix is all up, combine everything from short range to long range: personal networks, local networks, cellular networks, satellite networks.