IDS lecture 1
22 aug. 2013Information
Project, 30% of grade, deadline 1.Oct, 10-12 pages with font size 12pt. Deliver as PDF or DOC
Definitions
This subject is all about identifying and responding to intrusion of security goals like confidentiality, integrity and availability.
IDS: Automatically detect an intrusion and leave the handling to another system
IPS: Automatically detect and prevent an intrusion. Prevention can be active and passive. Passive would be measures like adding fixed firewall rules and applying patches. Active is when attacks are stopped on the fly determined by the detection algorithm. IPS apply both to entering and exiting traffic (extrusion detection)
Assumptions:
- There exists distinct evidence separating normal vs intrusive actions
- Data needed for decision is readable and available (this is often not the case)
Internet is "insecure by design", at least for integrity and confidentiality. Internet was originally designed to be very tolerant. A detection system can be looked at as a communication channel (see Shannon) with noise and thus a theoretical limit to how efficient it can be. We are close to the limit and it's important to realize we can never have 100% true positives. IDS/IPS are very resource heavy, and therefore often implemented in ASIC/FPGA hardware.
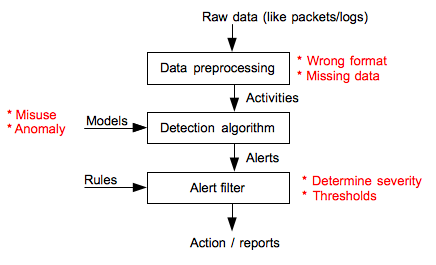
Model of a generic IDS/IPS system
- Preprocessing: input is raw data. Strategic located sensors is important when network is monitored. Can also be data such as logs, monitoring of API calls etc. It must be convert to a common format/feature vector. Formating is easy but the problem is missing data. It can be lost network packages or perhaps contex data not available digitally. Output is activities. More and more focus on content data vs meta data.
- Detection algorithm: The input can be different models and the processed data. The goal is to classify/separate between good and bad behavior. Anomaly detection depends a lot on context and require a lot of memory, and uses thresholds for normal/abnormal. The output is alerts.
- Alert filter: Is the alert important? What severity to assign? In this stage alerts are put in context. An alert can range from unimportant to critical depending on where it is observed and thus the need to apply and adjust the decision criteria. Apply automatic responses.
There are two primary ways to classify IDS/IPS systems:
By classification
- Host based (local logs and system calls)
- Network based (but sensors at strategic places)
- Application (like for big appliances like databases)
- Target based (integrity verification using hashes, and also trace calls within application)
By detection method
- Misuse detection: signature for every known attack. Problem is zero days and growing databases. most used but considered bad. Good for known bad stuff, polymorphic code can be problematic. Like blacklisting. False positives is a major problem.
- Anomaly detection, describe normal behavior, adapt over time. Using statistical methods, artificial intelligence, data mining etc. Requires a lot of tuning/oversight. Infrequent but normal traffic is a problem. Like whitelisting.
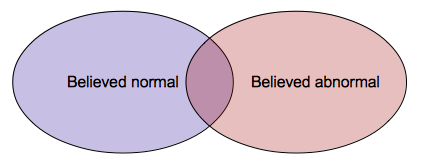
Overlap of good and bad activities
In any case, fast search is important because search through the whole database of good/bad things must be search through. Another problem are overlap between known good and known intrusive evidence as it can depend on context. Like port scanning: Usually a bad sign of reconnaissance, but it can also be an administrator testing the network or a user looking for shared resources. Both detection methods are often used in a product.
TCP/IP repetition
- IP-addressing: Classfull vs classless (subnetting), fragmentation, header of IPv4 and IPv6
- Layered model, OSI model (physical, link layer, network, transport and application)
- TCP vs UDP: Reliable vs speed, 3 way handshake, the flags (urg, ack, psh, rst, syn, fin + ns, cwr, ece), triangle delay vs reliable vs throughput. Usage of sequance numbers and acknowledge numbers.
- ARP (Address Resolution Protocol) binding MAC addresses to IP-addresses
- ICMP (Internet Control Message Protocol) with maintenance functions like "ping", "destination unreachable" etc.
Phases of an attack
- Planning: Define goals like denial of service, steal data, corrupt data etc. Plan how to get access like registering or going under cover.
- Reconnaissance: Discover vulnerabilities, port scanning (fast and slow, single or distributed), silent sniffing, open sources like forums and bug trackers.
- Attack: Denial of service focused at resource or protocol abuse (like smurf attack or syn flood), buffer overflow to get unauthorized code to run, plan a Trojan horse or use a backdoor, misuse of legitimate access, SQL injection attack, Unicode attack...
- Post attack: Cover tracks like deleting logs, penetrate deeper into network, gather, manipulate and/or destroy data, sell the access or just leave it (hacking for fun)
Lab 1 (Notes)
- Installing Wireshark and looking at TCP handshakes and termination. Also looked at TCP flags.
- Installing hping, a packet generator. See how easy it is to spoof an IP package.
- Installing nmap, a port scanner.