Digital forensics in a corporate context
19 apr. 2013This presentation continued from the forensics readiness. This lecture is followed by two guest lectures by Ericsson and BDO talking of basically the same thing from different perspectives
This lecture were held by Årnes working at Telenor. The dilemma in a corporate context is operational concerns being prioritized over sound evidence accusation.
Security threats and incidents
Social networks and trust, everything connected, private vs work data (workers using private equipment). Targeted attacks (Advanced Persistent Threats) like Ghostnet. The Athens affair where Vodaphone in Greece: lawful interception functionality in Ericsson AXE switches in mobile network were subverted to allow interception of high profile officials using root kit technology hiding it from technicians for a long time.
We remember the two important principles from digital forensics 1: Chain of custody and integrity, both bringing weight to evidence, and we also remember the order of volatility being an issue for integrity because it's never possible to keep everything.
We remember the focus of government/law enforcement versus commercial companies is different. The model for forensic investigation in a law enforcement role was:
- Identify (what happend)
- Acquire (collect evidence)
- Examine (look at the evidence)
- Analyze (build theories and use evidence to prove/disprove them)
- Report (present findings, for example in a court)
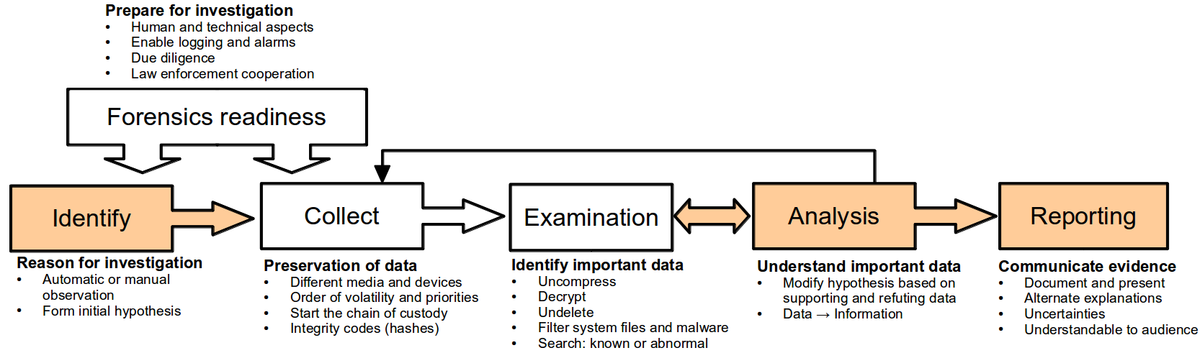
First we focused on "computer security incident handling". The steps now become:
- Prepare
- Analyze
- Recover
- Post recover activities
And we see the main difference comes to data accusation not being a priority, replaced with restore of normal operations.
We had some discussions of who to inform, including media, vendors, ISP, law enforcement (depends), and internal parties like leadership and other key personell. We should read NIST 800-61: Incident handling
We had two cases: In the first one the situation was our ISP telling us compromise and data exfiltration was seen against us, and what to do about it. Our group looked at options when we were told first, and the other group the case where ISP went directly to the police.
Dawn raid situations
Typical "first thing in the morning" to catch people off guard, typical for competition and tax, economic in general types of crime. Main steps are:
- Take full control and get hold of key personnel
- Avoid further evidence destruction by starting to gather it
- At the same time perform interviews on key personnel in order to check their stories against each other and to make sure they don't talk amongst themselves.
- Use trusted corporate technical resources to help in getting access
It can last from days to weeks, and it's a huge burden to companies. Forensics readiness is a way of preparing in order to minimize impact on business operations by being transparent, implementing forensically ready procedures for information management and accountability.
In case number two, a company was to be dawn raided in the following morning, and one group looked at preparations from the law enforcement while the other at the companies perspective given they knew it would happen (rumors)
Identity and access management (IAM)
So basically "who did what", integrating identification system for authentication in huge organizations, typically providers are Oracle, IBM and Microsoft, and we went trough a huge illustration of different terminology.
Identity management is how identification is done in an organization, ranging from procedures to technical components. Can be access cards, usage of passwords etc . Access management is protecting access to resources (confidentiality, integrity) using the established identity system.
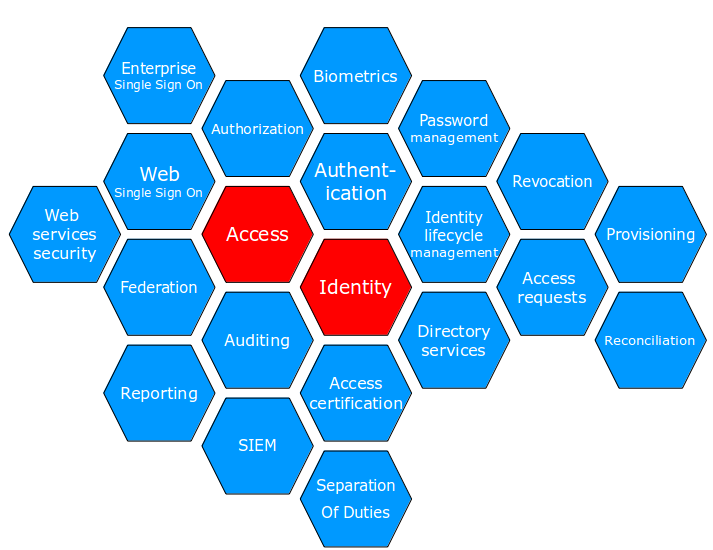
This illustration was shown. Not quite sure why it's designed the way it is, but we see terminology related to each other.
- SSO is "single sign on"
- SIEM is probably "Security information and event management"
- SoD is "Separation of duties"
- Federation: A federated identity in information technology is the means of linking a person's electronic identity and attributes, stored across multiple distinct identity management systems [Wikipedia]
- Directory services: Something like active directory where one can look up what access an identity possesses.
- Revocation: Removing access
- Provisioning: User provisioning refers to the creation, maintenance and deactivation of user objects and user attributes [Wikipedia]
- Reconciliation: Compare resource accounts in Identity Manager with the accounts actually present on the resources [Oracle]
The important takeaway is that IAM systems is a great tool for starting an investigation because it usually has audit logs of access centralized, and one can quickly see who is supposed to have access to certain objects. Per device logs must still be fetched from the devices (or dedicated log devices) for stuff like web-logs, database logs, application logs etc.