SST #5
19 apr. 2013Topics for today was user interface, unsafe endpoints and catch up from previously: vulnerability analysis
There were no lecture, but we had 4 student presentations:
- Trusted path: showing how trusted path between user and operating system is implemented in Solaris with focus on user interface. Separation of information zones, stopping information flow between zones and letting user know when talking (writing) to the OS.
- OWASP top10: injection, broken authentication, cross site scripting, insecure direct object references, security misconfiguration, sensitive data exposure, missing functional level access control, cross site request forgery, using known vulnerable components and unvalidated redirects and forwards.
- Transactional memory: Using techniques from database transactions, like write, check and commit in order to simplify deadlock sitations.
- Static analysis: Turned out to be about using tools to test compiled binaries for malware, ranging from checksum to tools visualizing call flow and properties from compiler.
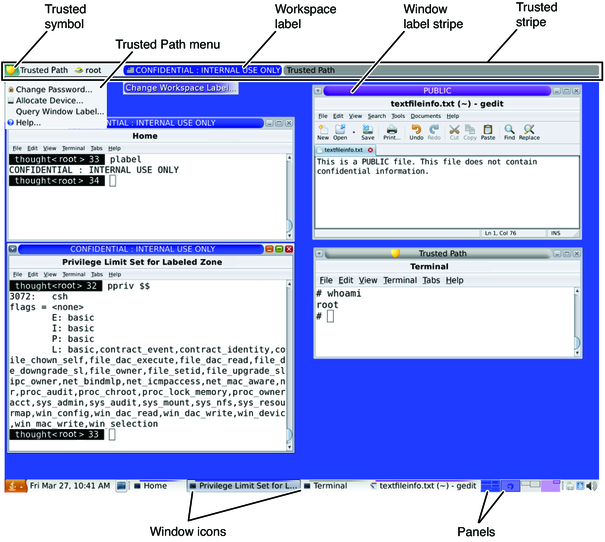
Image from docs.oracle.com showing the trusted stripe, window labels and symbol
Snarveier
Flere fra skole