Forensics Readiness
4 apr. 2013This lecture was held by Ausra Dilijonaite working at Mnemonic and doing a master thesis on "Enterprise Forensic Readiness". Two documents were posted as preparations: "A Ten Step Process for Forensic Readiness" (2004) and "A Theoretical Framework for Organizational Network Forensic Readiness (NFR)" (2007).
"maximizing the ability of an environment to collect credible digital evidence while minimizing the of an incident response"
"a major reason legal remedies are not pursued in cyber intrusion cases, is the cost and level of effort required for reactive investigations

Preparation notes
Forensics Readiness is about maximizing the potential of digital evidence by shifting focus from a reactive to proactive focus, and by doing that minimizing the resources required to handle an investigation if it occurs.

Benefits include:
- Protect potential evidence that might otherwise be lost due to organizational procedures, technicalities or active erasure. (Like quickly starting packet dumping, extra logging etc)
- Quick containment of evidence and procedures for minimizing disruption of business operations
- Deterring insiders from performing criminal acts (They know they will get cough)
- Collaboration with law enforcement showing due diligence (Openness around internal affairs)
But it requires:
- More administration..
- More training of personnel and working hours
- More infrastructure (storage, safe keeping)
- How to make sure key personnel does not abuse access power (backup administrators, log administrators, evidence planting)
Readiness for what exactly:
- Threats, extortion, stalking, harassment, identity theft
- Accidents (with or without negligence)
- Disputes, disagreements, malpractice (what was agreed upon, what price, terms and conditions)
- Property rights infringements (business secrets) and content abuse
- Fraud, money laundering, falsification
A 10 step procedure is outlined:
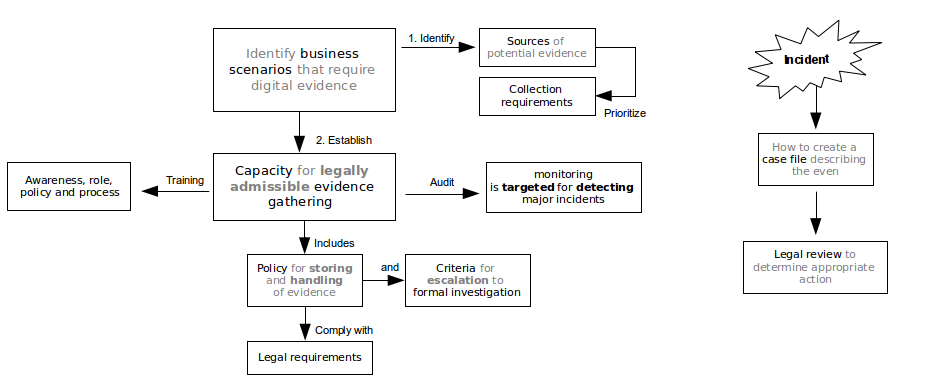
- Define the business scenarios that require digital evidence.
- Identify available sources and different types of potential evidence.
- Determine the Evidence Collection Requirement.
- Establish a capability for securely gathering legally admissible evidence to
meet the requirement. - Establish a policy for secure storage and handling of potential evidence.
- Ensure monitoring and auditing is targeted to detect and deter major
incidents. - Specify circumstances when escalation to a full formal investigation is required.
- Train staff, so that all those involved understand their role in the digital
evidence process and the legal sensitivities of evidence. - Present an evidence-based case describing the incident and its impact. (who, what, why, when, where and how)
- Ensure legal review to facilitate action in response to the incident.
The Network Forensics Readiness paper:
There are some concerns from organizational views that disclosure of incidents might lead to loss of reputation and consumer confidence leading to loss of revenue if disclosed, and also that law enforcement will seize computer equipment that might be critical for daily operations.
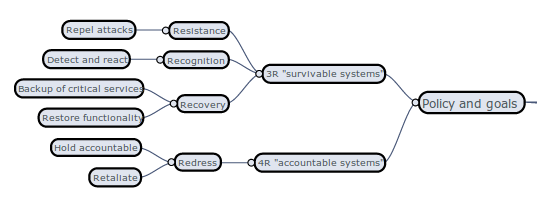
4R strategies of accountable systems (NIST):
- Resistance / avoidance
- Recognition
- Recovery (what happened? (small "f" forensics)
- Redress / retaliation (who did it? (BIG "F" forensics)
Main problem not enough (sound) data or time and skills needed to look through it?
What the heck is this supposed to mean? :)
Another benefit of having a forensics policy is
that the policy can be stated formally, in mathematical
notation, which allows for formal proof that a system is
capable of satisfying its forensics policy.
Terms
- Modus operandi
- Miscreant: A person who behaves badly or in a way that breaks the law.
- Deterrent: A thing that discourages or is intended to discourage someone from some act.
Lecture notes
- Willingness to be ready
- Is it cost effective?
- Proactive vs active vs reactive
- Military: "what", "who" and "keep running"
- Law: not so much "keep running"
- Commercial: not so much "what" and "who"
- Roles involved: response teams, managers, IT personnel, lawyers...
- Why: Bring to court and weight of evidence, avoid loosing evidence and reduce cost and time
- Funny cost formula: probability of not being caught, reward, cost of attack and cost of being cought
- Be aware of laws, especially legality of spying on workers (privacy)
- 10 list procedure
- 4R's