Digital Forensics I (part 2)
13 nov. 2012#3 lecture is moved from the 27th to the 20th of November. We had a presentation of two papers:
- Forensic analysis of social networking applications on mobile devices
- The persistence of memory: Forensic identification and extraction of cryptographic keys
Repetition from last lecture
Digital evidence: digital information acquired in a trusted way (evidence integrity) used in court.
Evidence integrity: How much digital evidence can be trusted. Chain of custody and usage of digital signatures
Evidence dynamics: Operations that can alter the digital evidence like writing, modifying, reading and deleting
Order of volatility: For how long data can be assumed to stay in it's current form. High order like RAM changes rapidly
Levels of abstraction: Data can be access at different abstraction levels ranging from raw binary data to highly processed encoded like the display of a document in word.
Evidence acquisition: Usually refers to the process of copying media via write blockers and generating check sums that can later be used to verify integrity.
Cyber crime: Common law, common procedure (laws) and availability (of response) are the 3 keywords.
Uncertainty in internet tracking: Time stamps with different sources and formats, stepping stone / proxy / VPN, Spoofing, NAT, service high-jacking (DNS, whois)..
Main topic: file system artifacts in Windows, Linux and Mac
- Encryption: Unreadable data without key and brute force might not be feasible
- RAID (Redundant Array of Independent Disks)
- HPA (Host Protected Area): Hide parts of the disk from the operating system
- SSD vs Magnetic: Different technology and increasingly more complex and smart drives
- File systems: Many kinds. Journaling might give additional hints. Important to get and understand the context of files.
- External media like floppies, CD, DVD, USB-sticks
- LBA vs CHS (old) addressing methods
File system abstraction levels:
- File system: Links to physical sectors on permanent memory (disk)
- File name: Separated from meta data since it can live elsewhere (linux has own file type called "folder")
- Meta data: Time stamps, permissions
- Raw data: Carving methods are always an option if the data hasn't been overwritten
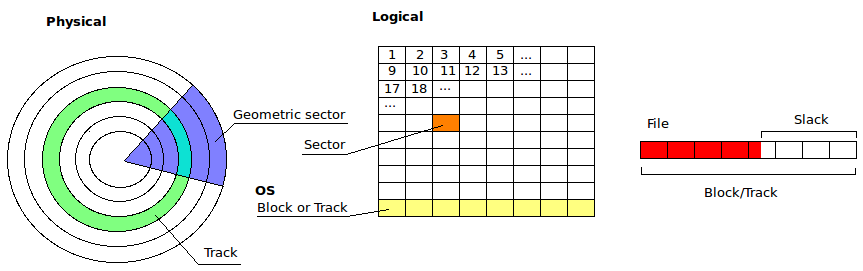
Minimum allocation unit
Traditional spinning magnetic harddrives used to be addressed with cylinder-head-sector. Now the internals of the drive is hidden from the operation system using Logical Block Address. The operating system is presented an interface to ask for any block (usually 512 bit). As disk space has increased, actual block size has also increased but the interface still emulate a 512 bit block. The addressable block is referred to as a sectors.
Operating systems use larger allocation units than sectors and they can vary in size. It's determined when the disk is formated, often during installation of the OS. In Windows file systems they are called clusters (or allocation units) and in Linux file systems they go by Block making the confusion total. Have a look at this definition at disktype.sourceforge.net
Slackspace:
When a cluster/block is overwritten with a file that is smaller and does not fill the entire allocation unit, the old data will (usually) stay unchanged. This information can be found and used.
Windows: FAT and NTFS
FAT has a File Allocation Table storing file name, MAC times (modification, access and creation) are stored as local time, file size and first cluster of data. When a file is deleted the first char of file name is overwritten and data clusters are marked unallocated.
NTFS has a Master File Table, and in addition to FATs meta data, it also includes a long file name. Dates are system time. On delete only data clusters are marked unallocated.
Mac OSX
HFS(+) can be capitalized and or journaled. It has an additional "backed up" timestamp. Metadata are stored in "forks" and it's rebalanced often leading to less likelihood of rebuild meta data once it has been deleted. The data itself is preserved
Unix
EXT2-3 uses inodes and the file structure is distributed with a common root (/). It has more kinds of of files: ordinary files, directories, symbolic files, IPC and devices (like memory, block and char devices)
The directory has a list of files within it and they all point to inodes. The inodes has permissions and ownership, MAC times and they refer to to blocks of data. They can be direct, single or double indirect.
Live forensics
OOV, use trusted tools (compiled yourself), system is rooted? Get passwords, encryption keys, study malware in memory, get latest changes not written to disk, hint off attacker by turning off system?, active sessions/connections.
Different levels of rootkits: binaries, libraries and kernel. trusted tools can't "override" kernel rootkits
get memory dump, process list, network connections
Memory: physical RAM, swap/paging area, crash dumps, hibernation file. Files and programs in memory. Copy data via ssh to remote machine (custom software, netcat and nc.exe), liquid nitrogen, reboot to custom OS to dump remaining/residual memory. Remember to preserve the chain of custody and hashes.
Interesting link dfrws.org