Digital Forensics I (part 1)
30 okt. 2012Forensics science is the application of scientific methodology in order to establish facts related to criminal or civil courts (criminal investigation) and can occur when a criminal action has been comited (post mortem) or while it's still ongoing. Examples could be
- Trace evidence like DNA analysis and fingerprints
- Interviewing for alibi and noting human behavior
- Physical calculations like firearm ballistics and force calculations in car crashed
Digital forensics deals with evidence in digital form (digital evidence). Evidence is defined as reliable artifacts that can support or refute a hypothesis about an incident. Analysis is based on statistics, logic and experiments. The nature of digital data, evidence dynamics in general meaning any influence that causes changes like relocation, obscuring and obliteration to evidence makes strictly scientific proofs difficult if not impossible to form implying a less strict approach is necessary. Still there are some concepts that are very important to follow: Integrity of evidence and chain of custody.
Digital forensics can take several forms:
- Computer: Find evidence on a single computer
- Network: Find evidence across a network?
- Device: forensics related to portable devices like PDAs, smartphones and pads, and can be great sources of access to a persons private information.
- Video/audio/image: Analyzing data contained in these formats in digital form. Important aspects are source verification, authentic/manipulated and finding interesting information hidden in huge amounts of data not easily understood by computers.
In addition a few methods were mentioned: Internet investigation: When using open sources like search engines, social web communities, registrars etc to collect data about something or someone. Note "investigation" since the acquisition of these data is not strictly controlled. Reverse engineering: is used to figure out the purpose and functionality of malware and discovering vulnerabilities in closed source software.
We discussed the dilemma related to forensic work versus incident response. Important aspects were having procedures already in place, and that employees would probably be more concerned with avoiding any loss rather than sound evidence collection. Evidence integrity is about making sure digital evidence is not modified since it was collected. Digital fingerprinting using secure hashes are used to prove integrity, and copying of digital data should if possible be performed with write blockers in place. Hardware is preferred over software blockers. Another related principle is chain of custody: Custody is kind of "who is in possession", and it's crucial to document what has happened since the evidence was acquired so that the evidence can't be deemed untrustworthy. This to ensure the evidence to be forensically sound
Related to evidence dynamics is the order of volatility. Volatile memory like RAM has the property that information it contains is gone when the power is lost (or soon after..) and it's important to realize that different medium ranging from the CPU cache to read only CD-ROM's have quite different levels of volatility. Collect the most volatile data first in most cases. Data collected in one part of the computer could cause changes in others, like when doing online dump of memory using custom software. The Heisenberg Principle states that it's (essentially) impossible to collect all data for analysis).
Another discussed issue has to do with two analyses of a cases, even given the same tools, might give major differences in conclusions. Dual-tool verification is the concept of using different tools to cover more ground. It could be expanded to include multiple individuals to perform the analysis to shed light on different aspects of the evidence. The process of digital evidence analysis is highly driven by intuition meaning the human skill of finding patterns (pattern recognition) and anomalies.
ACPO principles was mentioned, and in essence it's about forensically soundness and chain of custody.
Methodology
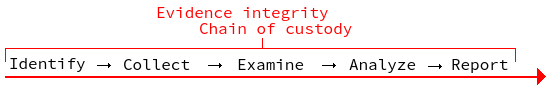
- Identify: What has happened, state problem, form hypothesis
- Collect: Collect the evidence. Often requires a court order and coordinated secret action to avoid intended destruction of important evidence
- Examine: Restore deleted files, filter out uninteresting files (like shared OS modules) / noise..
- Analyze: Use scientific methodology by testing hypothesis and finding evidence that can support or disprove them
- Report: Document the findings and present them. One important aspect of this is being an "expert witness" explaining the technical implications in court. Disprove "the trojan did it" arguments from the defendant. In court the testimony will be challenged for soundness. It's also important to document the the task given by supervisor so not to go outside of scope and of course document every step. Work has to be repeatable
Fighting cyber crime worldwide
It's impossible to fight cyber crime on a national level because the Internet is a global network. The Cyber Crime Convention (2001) is an initiative to agree on common ground on what is considered illegal activities online. This to avoid so called "safe-havens" or free zones. In cross border criminal cases (and Internet crime usually is) some new constraints come to play: jurisdiction and different criminal procedure laws. Norwegian police has jurisdiction in Norway, but can't operate in other countries and thus the need for cooperation. Criminal procedure laws are regulations on what can be legally done when suspicion is raised, even if it's illegal, like privacy considerations. The main problem with cross border cooperation is it's time consuming and not every country has signed these conventions.
Banking trojans were used to illustrate the problem. An attacker will usually try to hide his identity and location by compromising machines in different countries (to make police work harder) and using each machine as a stepping stone to confuse. Other methods like anonymity networks and manipulation of registrar information could also be used. There are passive and active methods to probe a source IP-address but given that the attacker probably won't be directly the visible address in combination with actively probing a professional hacker will alert him makes this very difficult. Luckily many criminals aren't really that skilled and will eventually make mistakes.
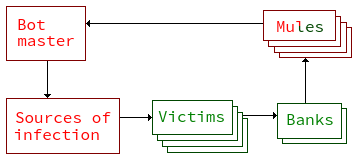
The goal is to capture the bot master and prosecute him. The source of infection could be a web page running vulnerabilities against the browser, and it could also include some update mechanism and or "commando control" server to keep track of infected machines. The bot master would use stepping stone and other methods to hide the connection to this server. Traces on victims machines would most likely direct at some source of infection. The trojan usually act when the victim is logged into the bank transferring money to mules, usually within the same country to avoid restrictions on money transfers. The mules withdraws the money and send it to the "bot master(s)" by some other means. The mules often don't know that what they are doing is illegal.
A last few words on evidence
Online evidence is especially difficult to control integrity of, and that's why much of the focus is at the chain of custody. Important sources are logs, caches, archives, and online profiles. Still, even if the evidence can be acquired there is still the uncertainty of "who's at the keyboard" (was it the trojan?), time stamps can vary greatly (time zone, miss configuration, or modification) adding complexity to timeline visualization and the information is scattered all over.
Interesting domains needing futher work
- Visualization of data: infographics
- Gathering data from "cloud source"
- Processing data using "cloud sources"

