IT Governance (part1)
23 okt. 201223th october 2012
Session 1: Chapter 1-5: Definitions, history, motivation and beginning of workflow...
What is IT Governance?
"Governance is the act of governing"
"Consistent management, cohesive policies, guidance, processes and decision-rights for a given area of responsibility" Wikipedia
IT is Information Technology and references "computer-based information systems" in this context. In other words:
Management and leadership of computer-based information systems
Important aspects are organisation, resources (human and equipment) and documentation. Best practices in IT governance are collected and standardized in ISO 27001/2 and form a Information Security Management System (ISMS) ..a framework. How to implement and operate ISO 27001/2.
Definitions and abbr. (modified) from ISO 27001
Asset
"Anything of value" - Can be tangible defined as abstract things like culture, trademarks,...
Information security
Availability, confidentiality (+ authenticity) and integrity (+ accountability and none-repudiation) of the defined assets
none-repudiation is the property "an action cannot be denied by any party"
Risk management Overall term for things to to with risk...
Risk assessment Risk analysis + evaluation
Risk analyses Systematic identification of source for and estimation of risks (for breach of information security)
Risk evaluation Comparing identified risk against some criteria to determine significance
Risk treatment Process of selecting and implementing measures to limit risk factors
Residual risk Remaining risk after implemented risk lowering measures are performed (risk treatment)
Risk acceptance Decision to accept a risk (there will always be residual risk, the difficulty lies in where to draw the line between risk reducing measures and cost (money, time, knowledge)
ISMS Information Security Management System
ISO International Standards Organization
ISO 27001 ISMS requirements
(former BS7799 (1995) adapted as ISO17799 (2000) and now ISO27001 (2008) )
ISO 27002 Code of practice
ISO 27003 Implementation guidance
ISO 27004 Metrics and measurements
ISO 27005 Risk management
ISO International Standards Organization: Multinational organization dealing with standardization
SoA Statement of Applicability: the parts of the 27k profile that applies to your business/organization
OWASP Open Web Application Security Project
PDCA "Plan Do Check Act"
UKAS "United Kingdom accreditation service"
SOX Sarbanes-Oxley act of 2002 (US law)
"Public Company Accounting Reform and Investor Protection Act" as an reaction to major corporate and accounting scandals
SA Security Assurance: How well we trust the security (of equipment like network equipment and KVM extenders, and services - See Common criteria ISO 15408. Evaluated to "evaluation assurance levels" 1-7)
QA Quality Assurance: Organizational procedures, tasks and responsibilities. ISO 9000
Implementing the ISO
Starting to implement ISO 27k is time consuming, usually takes 1-2 years to get certified if it is prioritized. It's a never ending process aiming to continuously improving and adapting to changes in the operating environment. Getting certified is recommended but not necessary for security obviously. Motivations for getting certified could be some kind of business/competitional advantage, legal requirements or simply to manage risk. The whole process is illustrated in the professors lecture on slide 1.1.2-#2 and 1.1.2-#3 (yellow boxes in #3 are document output)
Examples of legal requirements are the Norwegian privacy law "personopplysningsloven". The basel 2 regulates banking (how much in reserve, and risk allowance). Other mentioned are The Combined Code and Sarbanes-Oxley Act
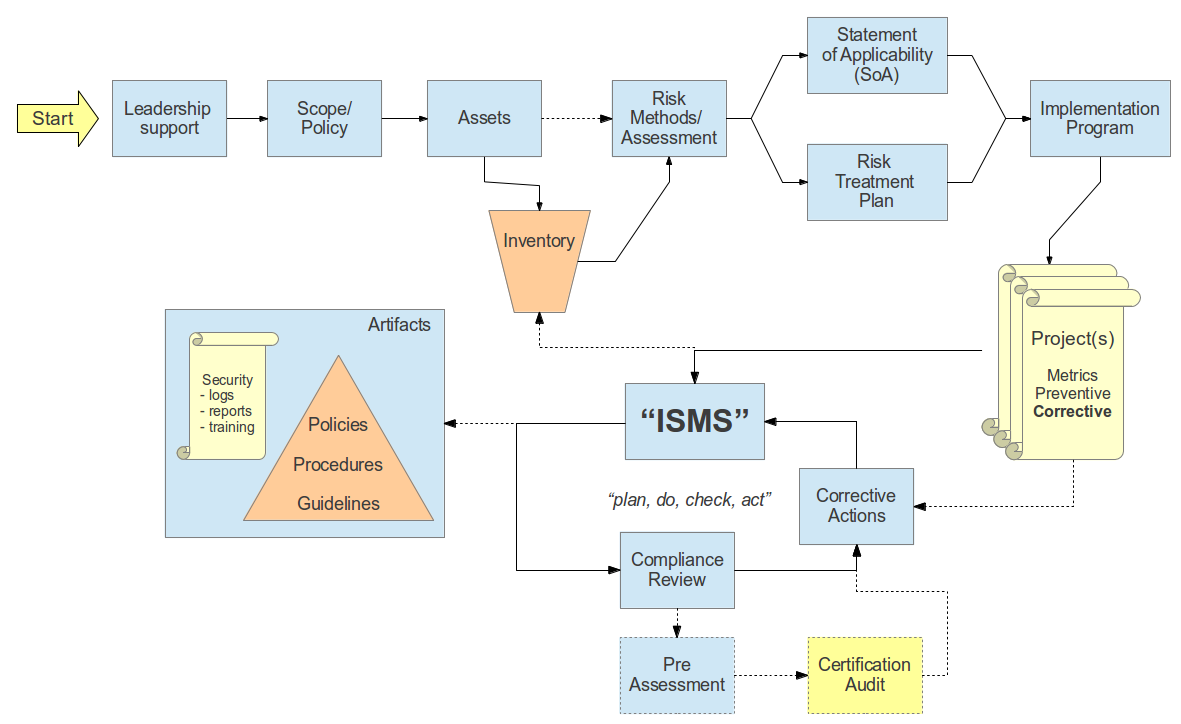
iso27001security.com source
There are 4 main areas of ISO 27001 (work cycle)
- Plan: Establishment
- Do: implementat and operate
- Check: monitoring and review
- Act/Reviewing: maintaining and improving
The first step is very important. The decision to start a process as complex as this one has to be a strategic decision made at the highest level in the organization, typically the board/Chief executive officer, and the next thing to do is to clarify the scope of the implementation adjusting the ISO27k with respect to security requirements, current security processes, size and structure of the organization. The output of this initial work would be to clarify the road ahead and a policy describing the rationale and scope of the work to continue.
The policy should be small (2 pages) revised 1-2 times a year, responsibilities, and the goal of implementation.
The "way ahead", implementation plan, need to consider cost estimate and deadlines.
In a perfect world this kind of process would be initiated top down. In reality it usually has to be pushed up by roles responsible for security, and that's why some thoughts regarding "What impact would a computer system breakdown result in?" be usefull:
- Loss of competitive related information (business secrets)
- Loss of customer/user related information (privacy - reputation)
- IT as business accelerator or even enabler - denial of service?
- Legal requirements (avoid prison/fines)
Threats can be
- External
- Cyber activists: political, social, environmental etc
- Cyber pranks/skill showoff: Scriptkiddies
- Cyber crime: Econnomic motivated attacks (but usually limited in damage - a parasite does not want to kill its host)
- Cyber war/terror: Attacks with damage as main goal (hurt the opponent)
- Cyber activists: political, social, environmental etc
- Internal
- Unhappy employees (employees being fired, bribed or has private agendas)
- Unhappy employees (employees being fired, bribed or has private agendas)
- Development/deployment
- Design: Default allow/on vs. default deny/off, security from the beginning vs. added as a "patch". KISS
- Code: More code and increasing complexity equals more errors, input validation leading to buffer overflows or database attacks
- Implementation/configuration: Even historically proven tools can be configured badly (firewalls, SSL
- Design: Default allow/on vs. default deny/off, security from the beginning vs. added as a "patch". KISS
Who need to participate? (in IT Gov work)
The board, CEO, (CIE/CTO), Security manager, IT department..
It's important to fulfill the information requirements to the stakeholders (they give input on risk threshold)
It's also important to realize there might be issues with the current IT department trying to hold on to the "old way"
Assets
Next in the process all important assets must be defined, risk assessed for each of them, and a decision on acceptable risk must be carried out.
Group assignment
In class: Started with a case "Flatfisk ASA" defining stakeholders, valuables/assets, possible damages to assets and Threat agents. "homework": The first group assignment will continue with this case. Waiting for group divisions and tasks...
Delivered by 17:00 mon 5th, one pdf on fronter. Multiple choice from chapter 5-12+14,15 must also be performed within this date.