IDS labs
6 sept. 2013For the labs in intrusion detection I installed a virtual machine running Fedora 19. I then deleted that machine because the package manager "yum" kept freezing on me, and instead I built another virtual machine from a Linux distribution called "Mint"..
Misc
Wireshark (Ethereal)
Install from wireshark.org or if you got linux with apt-get:
sudo apt-get install wireshark
The version for MAC is a bit ugly since it's using an older X11 window, but it works...
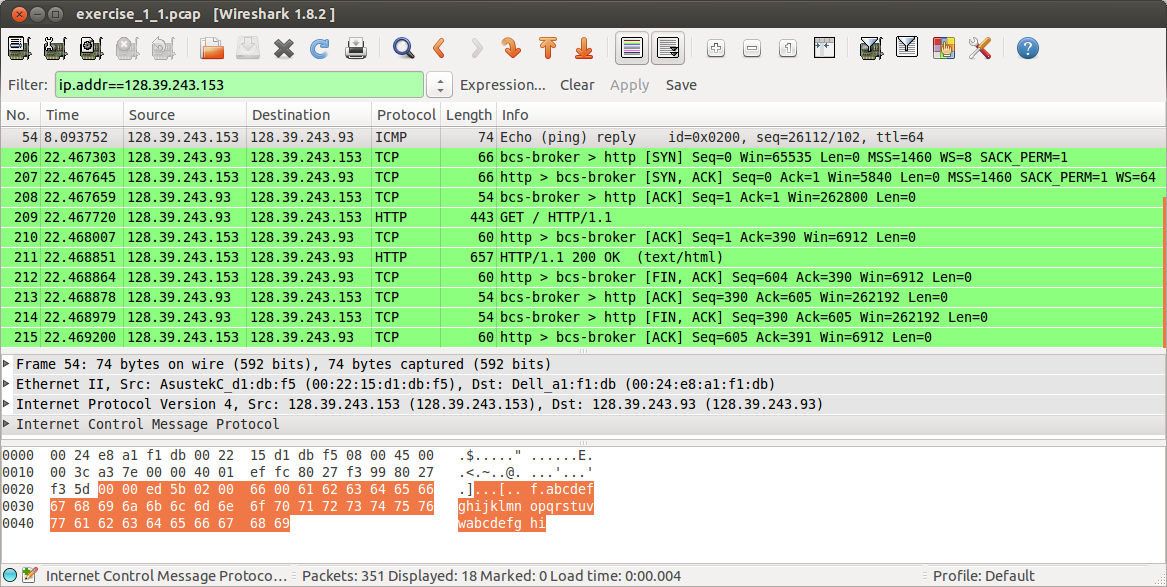
Hping
Install from hping.org or using apt-get:
sudo apt-get install hping3
hping -1 -a 10.0.0.1 -I device -c 10 destination # spoofing 10 ICMP packages
hping -c 10 -I device -s 30000 –p +0 -S destination --keep # 10 packages
Nmap
Install from insecure.org or do:
wget http://nmap.org/dist/nmap-5.61TEST5.tar.bz2
sudo apt-get install g++
tar jxvf nmap-5.61TEST5.tar.bz2
cd nmap-5.61TEST5/
./configure
make
make install
sudo apt-get install zenmap
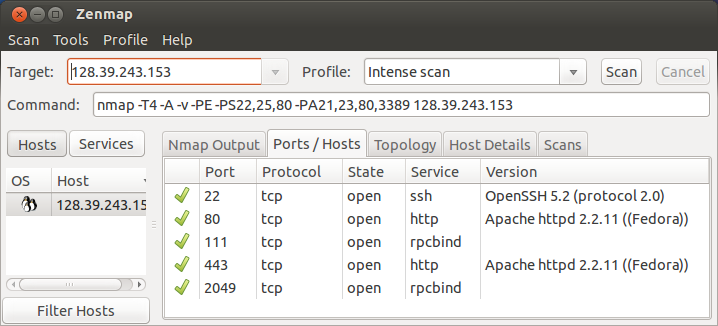
Snort
Snort has some prerequisites: libpcap from tcpdump.org and daq available from the snort homepage snort.org together with the snort source files. I also had to install bison and flex as they were dependencies needed and asked for. Installation is quite regular:
tar -zxvf <filename>
./configure
make
sudo checkinstall
Even after installing libpcap 1.4 manually I still got the error "Libpcap library version >= 1.0 not found" when running the "./configure" on daq. I therefore removed an old version of libpcap (0.8) using
dpkg -l | grep libpcap
sudo apt-get --purge remove libpcap0.8
It still did not work, so I installed Wireshark using apt-get (which includes libpcap) and now it finally worked (and I got both 1.4 and 1.3 installed). There is probably a correct way to handle this, but the way I see it, building from source is a messy way to manage software.
Config and logs
mkdir /etc/snort # put *.conf, *.config & *.map files here
mkdir /etc/snort/so_rules # ??
mkdir /etc/snort/rules # ??
mkdir /etc/snort/preproc_rules # ??
mkdir /var/log/snort # ??
mkdir /usr/local/lib/snort_dynamicrules # put precompiled rules
Snort ./configure options
./configure --enable-ipv6 --enable-gre --enable-mpls --enable-targetbased --enable-decoder-preprocessor-rules --enable-ppm --enable-perfprofiling --enable-zlib --enable-active-response --enable-normalizer --enable-reload --enable-react --enable-flexresp3
Additional libraries: libdnet-1.12 and pcre-8.33 had to be installed manually, and then it started complaining about daq_static not being found. Installed it (again?) and then needed to find zlib!
Then it kind of succeeded I think. Got "--enable-ipv6" and "--enable-decoder-preprocessor-rules" unrecognized though.
Usage
First thing that pops up is a message that libdnet.1 is not found, and it can be fixed by making a symbolic link
sudo ln -s /usr/local/lib/libdnet.1.0.1 /usr/lib/libdnet.1
snort –vde –i eth0 # run as print-to-terminal packet logger
snort –vde –i eth0 –l /var/log/snort # packet logger and logging to this folder
snort –vde –i eth0 –c /etc/snort/snort.conf # run as an IDS using this config file (remove -v for avoiding printing to terminal)
<installation and usage of Bro>
<installation and usage of Suricata>